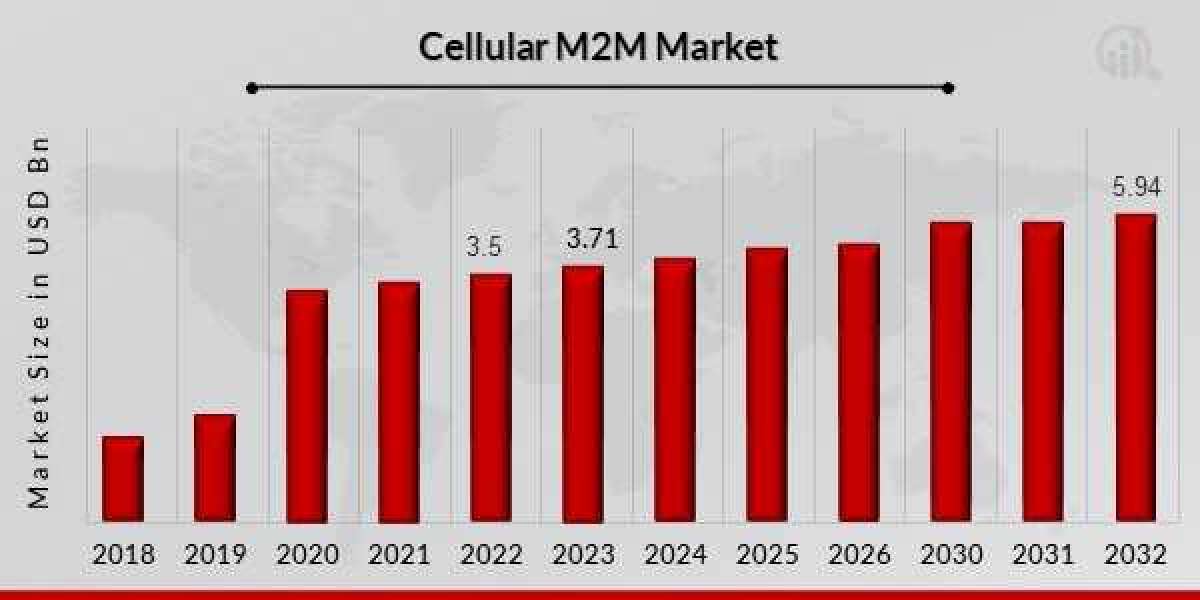
In the ever-evolving landscape of technology, cryptographic systems play a pivotal role in safeguarding information, ensuring privacy, and enabling secure communication. As briansclub dive into the intricate world of cryptography, this article will unravel the complexities, applications, and future prospects of cryptographic systems.
The Foundation of Security: Understanding Cryptography
Cryptographic systems are the bedrock of modern cybersecurity, providing a robust framework for securing sensitive data in transit and at rest. At its core, cryptography is the science of encoding and decoding information to protect it from unauthorized access. This involves the use of algorithms and mathematical functions to transform data into a format that is unintelligible without the proper key.
Types of Cryptographic Systems
1. Symmetric Cryptography
Symmetric cryptography involves the use of a single key for both encryption and decryption. This key must be kept confidential between the communicating parties. While highly efficient, symmetric cryptography faces challenges related to key distribution, as securely sharing the key among users can be a logistical hurdle.
2. Asymmetric Cryptography
Asymmetric cryptography, on the other hand, utilizes a pair of keys: a public key for encryption and a private key for decryption. This eliminates the need for a shared secret key, simplifying key management. Asymmetric cryptography forms the foundation for secure communication over the internet, enabling the creation of digital signatures and facilitating secure key exchange.
3. Hash Functions
Hash functions are integral to cryptographic systems, providing a one-way transformation of data into a fixed-size string of characters. This irreversible process ensures data integrity and authenticity. While hash functions are not designed for encryption, they are crucial for creating digital signatures and checksums.
Applications of Cryptographic Systems
The widespread adoption of cryptographic systems extends beyond mere data protection; it is a cornerstone of various applications across industries.
1. Financial Transactions
Cryptocurrencies, such as Bitcoin and Ethereum, rely on cryptographic systems to secure transactions and control the creation of new units. Blockchain, the underlying technology of most cryptocurrencies, employs cryptographic hashing to link blocks of transactions in a tamper-evident manner.
2. Secure Communication
In the era of digital communication, ensuring the confidentiality and integrity of messages is paramount. Cryptographic protocols like SSL/TLS enable secure communication over the internet, safeguarding sensitive information exchanged between users and websites.
3. Identity Verification
Biometric data, such as fingerprints and facial recognition, is increasingly used for identity verification. Cryptographic systems help secure biometric templates, ensuring that even if the data is compromised, it cannot be reverse-engineered to reconstruct the original biometric information.
The Future Landscape of Cryptography
As technology advances, so do the challenges faced by cryptographic systems. Quantum computing, for instance, poses a potential threat to existing encryption algorithms. To address this, researchers are actively exploring post-quantum cryptography, which aims to develop algorithms resistant to quantum attacks.
1. Post-Quantum Cryptography
Post-quantum cryptography focuses on developing encryption algorithms that can withstand the computational power of quantum computers. As the race to quantum supremacy intensifies, the need for cryptographic systems resilient to quantum attacks becomes increasingly urgent. Researchers are exploring lattice-based cryptography, hash-based cryptography, and other approaches to secure our digital future.
2. Homomorphic Encryption
Homomorphic encryption is a cutting-edge cryptographic technique that allows computations to be performed on encrypted data without decrypting it first. This revolutionary approach has profound implications for privacy, enabling secure data processing in cloud environments while keeping sensitive information confidential.
3. Zero-Knowledge Proofs
Zero-knowledge proofs offer a way to verify the authenticity of information without revealing any details about the information itself. This cryptographic concept has applications in privacy-preserving technologies, such as anonymous authentication and confidential transactions.
Conclusion
In the ever-evolving landscape of technology, cryptographic systems serve as the guardians of our digital realm. From securing financial transactions to enabling private communication, the applications of cryptography are diverse and crucial. As brians club navigate the challenges posed by quantum computing, emerging cryptographic techniques like post-quantum cryptography, homomorphic encryption, and zero-knowledge proofs are paving the way for a more secure and private digital future. Cryptomind, indeed, delves into depths of cryptographic systems, unraveling their intricacies and shaping the path forward for a resilient and secure digital ecosystem.